Ransomware is a type of malicious software that infects a computer and restricts users’ access to it until a ransom is paid to unlock it. It does not only target individuals but also organizations and enterprises including healthcare.
In the last few months, there has been a string of ransomware attacks in healthcare facilities across US. MedStar Health, Chino Valley Medical Center, Desert Valley Hospital, Alvarado Hospital Medical Center and King’s Daughters’ Health have all reported varying degrees of malware or ransomware attacks leading US and Canada to issue a joint ransomware alert on March 31 2016, discouraging paying cyber attackers.
How does it spread?
It is often spread through phishing emails that contain malicious attachments or through drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website and then malware is downloaded and installed without the user’s knowledge.
Crypto ransomware, a malware variant that encrypts files, is spread through similar methods and can also spread through social media, such as Web-based instant messaging applications. Additionally, newer methods of ransomware infection have been observed. For example, vulnerable Web servers have been exploited as an entry point to gain access into an organization’s network.
Some ransomware can also spread offline. Samsam and Maktub Locker are new strains of ransomware that encrypt anything and everything it has access to even if the network connection is shut down.
How to detect your system security has been compromised?
The main difference between ransomware and traditional malware is that you often know that you have been infected because the malware tells you this. Typically, these alerts state that the user’s systems have been locked or that the user’s files have been encrypted. You can receive intimidating messages such as:
- “Your computer has been infected with a virus. Click here to resolve the issue.”
- “Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
- “All files on your computer have been encrypted. You must pay this ransom within 72 hours to regain access to your data.”
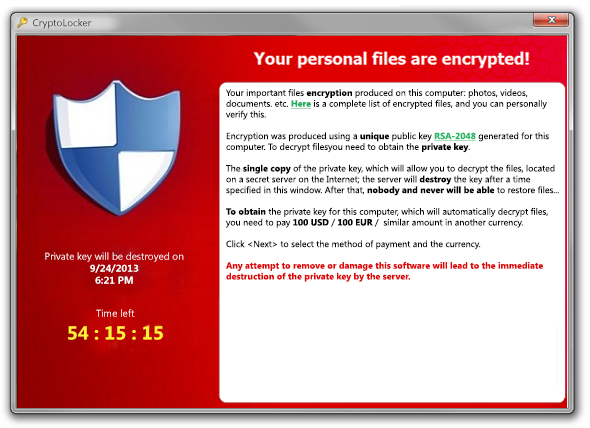
Example of Ransomware Alert
Users are told that unless a ransom is paid, access will not be restored. The ransom demanded from individuals varies greatly but is frequently $200–$400 dollars and must be paid in virtual currency, such as Bitcoin. Paying the ransom does not guarantee the encrypted files will be released; it only guarantees that the malicious actors receive the victim’s money, and in some cases, their banking information. In addition, decrypting files does not mean the malware infection itself has been removed.
How dangerous is it?
Ransomware known as MSIL/Samas.A seeks to encrypt data on entire networks, which is an alarming change because typically, ransomware has sought to encrypt data one computer at a time. New strains of this virus also spread offline. While most healthcare facilities have been able to continue their day-to-day operations some have had to go offline for an extended period of time affecting patient care. It’s hard recovering from a ransomware attack without professional help, which can be costly for smaller practices. In this case prevention is the best strategy.
Solution
Infections can be devastating to an individual or organization, and recovery can be a difficult process that may require the services of a reputable data recovery specialist.
US-CERT recommends that users and administrators take the following preventive measures to protect their computer networks from ransomware infection:
- Employ a data backup and recovery plan for all critical information. Perform and test regular backups to limit the impact of data or system loss and to expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Use application whitelisting to help prevent malicious software and unapproved programs from running. Application whitelisting is one of the best security strategies as it allows only specified programs to run, while blocking all others, including malicious software.
- Keep your operating system and software up-to-date with the latest patches. Vulnerable applications and operating systems are the target of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker.
- Maintain up-to-date anti-virus software, and scan all software downloaded from the internet prior to executing.
- Restrict users’ ability (permissions) to install and run unwanted software applications, and apply the principle of “Least Privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through the network.
- Email is a commonly used method to distribute ransomware. Attackers target victims with cleverly spoofed emails that appear to originate from someone the victim knows. The emails have malicious attachments which when opened results in the ransomware being downloaded on the victim’s system.One of the most effective ways for an organization to blunt this threat is to validate the origin of an email before it is delivered to the intended recipient. For information on safely handling email attachments, see Recognizing and Avoiding Email Scams.
- Ransomware is often distributed through malicious advertisements served up to users when they visit certain sites. Malvertisements allow attackers to target victims based on their browsing habits, location, demographic information, device characteristics, and other criteria. Blocking ads from being delivered on user systems or preventing users from accessing certain sites can diminish this risk somewhat. Follow safe practices when browsing the Web. See Good Security Habits and Safeguarding Your Data for additional details.
- Do not follow unsolicited Web links in emails. Refer to the US-CERT Security Tip on Avoiding Social Engineering and Phishing Attacks for more information.

Individuals or organizations are discouraged from paying the ransom, as this does not guarantee files will be released. Report instances of fraud to the FBI at the Internet Crime Complaint Center.
P.s : In hindsight, the author of this post was a victim of ransomware in 2012 but only realized it recently while researching for this article. If only she knew the warning signs then. She paid 150 pounds. Hopefully, this article will help others avoid a similar fate.

Join the Discussion!